What does Dynamic Case Management have to do with the 2016 election?

What do Dynamic Case Management and BPM Software have to do with the 2016 presidential election?
Truth be told, not all that much. But tis the season for election related blogs so this is my attempt at it:
The election has been front and center for the past 12 months. Today most of us are just happy it’s finally over. The oft overlooked topic from this election was the role that cybersecurity, or lack thereof, played in determining the 45th President of the United States. I won’t pretend to understand the electorate; however, it’s undeniable that the leaked Clinton campaign emails played a central role in ultimately deciding the outcome of the race.
For those who don’t know what I’m talking about (or have been asleep for the past few months): a malicious actor hacked the emails of Clinton Campaign Chair John Podesta. The emails, over 56,000 of them, date back to 2008 and have been published on Wikileaks in 36 batches over the past month. The emails are all private in nature, show the innerworkings of a massive political campaign, and were certainly not meant for public consumption.
Podesta’s email was likely hacked sometime around March 19th of this year when he received what looked like an email from Google regarding his gmail account:
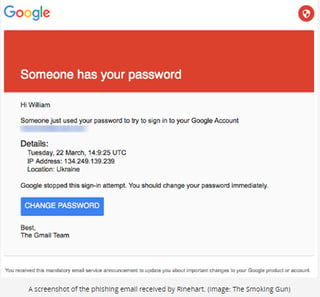
Unfortunately for Mr. Podesta that email wasn’t Google. In fact, it was a hacker on a phishing expedition and Podesta was the white whale. We now know that in addition to the Podesta hack there 108 email addresses targeted on the hillaryclinton.com domain. A political campaign is relatively small compared to a Fortune 500 company. Imagine a multi-national Bank or a large Health Insurer with tens of thousands of employees and millions of customers. Imagine the impact when one of these organizations gets hacked?
The reality of today’s cyber environment is frightening:
- Cyber threats on critical infrastructure are growing at over 30% per year
- Cybercrime rates (reported) are growing at 39% per year
- 7% of US companies lost > $1M (reported) from cyber-attacks
- 19% of US companies lost between $50,000 and $1M from cyber-attacks.
- 8M network encroachments were reported in 2014, an increase of 50% year-over-year
- Cyber analysts only have the capacity to research 20% of the data in the enterprise to mitigate/eliminate threats
How can we prevent this type of attack and how can we apply Dynamic Case Management and BPM Software to the solution?
We at srcLogic developed a Cyber Case Management solution on the PEGA 7 Platform. The srcLogic solution combines the power of PEGA 7 with srcLogic’s Pega development skills and domain knowledge gained from working with the leading cyber minds in the world. Rather than approach the problem at the network or device level, our solution provides enterprise visibility and automation of the Ops Center to answer the fundamental question: “Am I having a good day or bad day?”
Organizations everywhere, be they Fortune 50 or presidential campaigns have numerous security applications yet most lack a true holistic solution that automates the full spectrum of cyber processes – from incident report to investigation to signature release.
srcLogic is leading the charge in automating and providing visibiility into the cybersecurity mission. Contact us to learn more about applying Dynamic Case Management to the cyber security challenge.
